University of Bahrain
Scientific Journals
11. International Journal of Computing and Network Technology
- UOB Journals
- →
- 11. International Journal of Computing and Network Technology
JavaScript is disabled for your browser. Some features of this site may not work without it.
11. International Journal of Computing and Network Technology
Browse by
ISSN 2210-1519
DOI: dx.doi.org/10.12785/ijcnt
Managing Editor A. Y. M. Al-Omary
Email: ijcnt@uob.edu.bh
Frequency: 3 issues annually
No Publication Fee
The International Journal of Computing and Network Technology (IJCNT) is a is a peer-reviewed International Journal that publishes technical papers describing recent research and development work in all aspects of computing and computer networks. Papers must be written in English. They must not have been previously published and should not be under consideration for publication elsewhere. The frequency of International Journal of Computing and Network Technology (IJCNT) is four issues per year. It has both print and online versions.
In order to be considered for publication, your introduction should clearly explain the novelty, urgency and originality of the research in your article.
Plagiarism, or copying text or results from other sources, is unethical behavior and is not tolerated at this journal. All manuscripts will be checked for originality using the CrossCheck database. For more information on CrossCheck please visit http://www.crossref.org/crosscheck.html
Manuscripts submitted for publication must be in English and should be submitted via the web.
There are no page charges for publishing in this journal.
The International Journal of Computing and Network Technology publish articles which contribute new techniques and results in all areas of networking and computing. Topics of interest include, but are not limited to:
Editor-in-Chief
Managing Editor
Editorial Board
International Journal of Computing and Network Technology (IJCNT) is a peer-reviewed International Journal that publishes technical papers describing recent research and development work in all aspects of computing and computer networks, including the development of electronic design automation tools.
Authors are requested to follow the directions presented in the following
 IJCNT template.docx and fill the following
IJCNT template.docx and fill the following
 SPC copyright.pdf and then submit through "Submission Button"
SPC copyright.pdf and then submit through "Submission Button"
All manuscripts submitted to International Journal of Computing and Network Technology (IJCNT) are subject to peer review and must meet academic standards. Submissions will be, first, considered by an editor-in-chief, and then be reviewed by anonymous reviewers. Once the author submits any manuscript, an acknowledgment shall be sent to the author along with a technical paper for peer-review. The concerned manuscript shall be simultaneously reviewed by our extensive internal review/ referee network. The terms and conditions that behold any general reviewer/referee shall also hereby levied upon the peer-reviewers.
Referees are formal reviewers whose comments and opinions will form the basis upon which the Editor will decide whether or not to publish the paper, and with what changes. International Journal of Computing and Network Technology (IJCNT) requires that referees treat the contents of papers under review as privileged information, not to be disclosed to others before publication. The referees are protected from personal interactions with the author by withholding their names. The Editors decision is always based on all the reviews received, but mixed reviews present the need for the exercise of editorial judgment. Thus, the final decision for acceptance or rejection lies with the Editor. The review process shall ensure that all authors have equal opportunity for publication of their papers.
Review Steps
All manuscript will be assigned to more than one reviewer through 5 steps. As soon as we receive an article, the Editorial office will Pre-Review your manuscript in one week. The officer will check whether the manuscript is valid and language is fluent and necessary factors are all included. The officer will also cross check the article in crossref database in order to avoid plagirsm. The following is a formal review process accomplished by other official reviewers for one month. It is decided by Editor-in-Chief in one week whether your manuscript is accepted or not. All submitted papers will be reviewed in about six weeks.
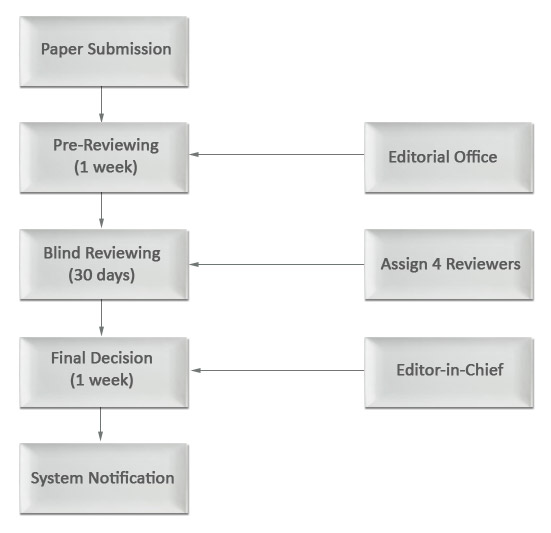
Type of Peer Review
This journal follows blind reviewing process, where both the referee and author remain anonymous throughout the process.
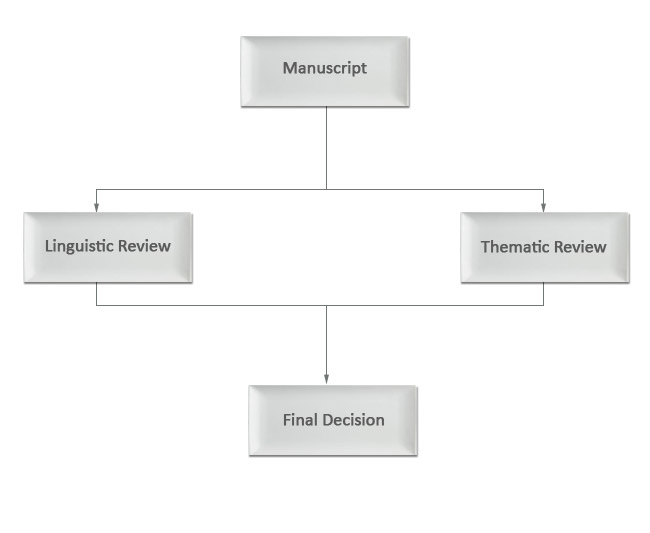
Formal Conditions of Acceptance
Each article submitted to us will be reviewed by at least 2 reviewers. Moreover the papers will be checked for linguistic consistency. Thematic review will decide whether to accept or reject according to the originality, significance for theory and practice, quality of content and presentation of submitted paper.
This journal is indexed by these worldwide databases:
- Google Scholar
- Gale, a Cengage Company
- EBSCO
Volumes within this journal
-
2019
Recent Submissions
-
(2019-09-01)Smartphones energy consumption and management have become a major issue all over the smartphones research and developing (R&D) centers. On smartphones, the researches must achieve the wide requirements of the power drawn ...
-
Optimal Utilization of Hybrid Renewable Energy System with Incentive Based Demand Response Program (2019-09-01)- Demand response plays a vital role in electricity market to maintain energy balance between supply and load. In this paper Optimal Utilization of Hybrid Energy System with Incentive Based Demand Response Program (DRP) ...
-
(2019-09-01)Macula is one of the very important landmarks in the human retinal image. Detection of macula is essential in the classification of some of the ophthalmologic diseases and for the feature extraction process in the ...
-
(2019-09-01)The Internet of Things (IoT) is one of the most promising technologies that seeks to improve quality of life by providing smart civic amenities. Several smart application domains that are envisaged include agriculture, ...
-
(2019-09-01)Cell based Machine-to-Machine (M2M) infrastructure is one of the key internet of things (IoT) empowering advances with immense market potential for cell specialist organizations sending 4G long haul development (LTE) ...
-
(2019-05-01)In wireless communication networks, the main thing is to achieve high data rates and to minimize the noise. As compared to 4G which supports 100 Mbps the 5G supports 1 Gbps data rates. By using multiple users, NOMA can ...
-
(2019-05-01)In this paper, a modified approach for frequency permutation of speech signal has been designed implemented and verified based on MATLAB Simulink. A separate permutation of real and imaginary parts of the frequency component ...
-
Optimization and Economic Analysis of Standalone Hybrid PV-Biomass-Hydel Energy System Using HOMER (2019-05-01)This study proposes optimization and economic analysis of standalone PV-Biomass and Hydel as a hybrid energy system that also includes diesel generator and battery array as back up source of power. This off-grid system ...
-
(2019-05-01)An automation system for monitoring the kitchen grocery items/cooking ingredients is presented in this paper. We are busy with our job/education/business, due to them sometimes we are not aware about the cooking ingredients ...
-
(2019-05-01)Higher data rate and increased capacity are the primary challenges of the next Generation mobile network infrastructure. In order to address such issues, Millimeter wave (mmWave) communication technology can play a vital ...
-
(2019-01-01)In this paper, different heuristics for cross-layer optimization for vehicular ad-hoc network are reviewed and analysed. Up to a large extent safety issues and traffic congestion in daily life can be resolved by integrating ...
-
(2019-01-01)One of the most rapidly advancing available imaging techniques is Magnetic resonance imaging (MRI). This technique has many side effects can be digested in to main categories: The first is the High Magnetic field effects: ...
-
(2019-01-01)Smart cities has developed in urban areas and are interconnecting every part of the city and offering enormous smart services to make the human life easier and convenient. The smart services are a result of data streams ...
-
(2019-01-01)Security and privacy have been considered a corner stone in all electronic transactions nowadays. People are becoming very cautious when conducting electronic transactions over internet. One of the major issues that frightens ...
-
(2019-01-01)In this paper, a new compact design of Ultra Wideband (UWB) fractal antenna is presented. The antenna geometry is described by means of a spline curve and a rectangular slot. The bandwidth of antenna has been designed in ...
-
(2018-09-01)Hidden node problem sometimes referred to as frequent packets collision that mostly leads to loss of packets is no longer new in wireless networks because it affects the previous IEEE802.11 standards. The new IEEE802.11ah ...
-
(2018-09-01)Serverless computing has emerged as a new compelling paradigm for the deployment of applications and services. It represents an evolution of cloud programming models, abstractions, and platforms, and is a testament to the ...
-
(2018-09-01)Motivated by the need to overcome dynamic traffic congestion problems and driving safety issues, lane keeping control of vehicles has become a very active research area and is a driver-assistance vehicle feature that ...
-
(2018-09-01)Cloud security mitigation techniques has not reached the level of transparency and hence, the journey of understanding and accepting cloud computing services still remains uncharted for many organizations or individuals. ...
-
(2018-09-01)Packet Scheduling (PS) is essential in Long Term Evolution (LTE) cellular system to handle huge traffic via allocating common resources among users. The main target of PS, in LTE systems, is the Radio Resource Management ...